As our world reliance on electronic connection and communication is accelerating, cyber attacks are on the rise along with
counter measure solutions in the form of endless new cyber security companies, consultants, expertise, software and hardware
aimed at protecting individuals, assets, corporations and even nation states.
However, even with all the tools and increasing cyber budget at our disposal, there is always one constant weak link:
The Human element in the so called Cyber Kill Chain.
It is this human element that can defeat the most sophisticated defence systems and it is why the use of Phishing and
Spear Phishing attacks are so prominent and successful.
Those attacks exploit human emotion, ignorance and credibility to bypass defences in tricking users to follow poisonous steps:
Clicking on links, opening documents, accepting/ignoring security warnings and good practises, installing software, etc.
They all attempt to install Malware/Backdoors to steal data and/or cripple the users' IT environment.
Because of the prevalence of those attacks and their high success rate, it is important to have an Anti-Phishing framework
that is tailored to the business' mode of operation it is trying to protect.
Although different medium are used to deliver such attacks: emails, phone calls (Vishing), physical social engineering, etc.
they can always be divided in 2 types: generic or targeted.
Phishing is Generic
Spear Phishing is Targeted.
An Anti-Phishing framework should therefore differentiate and include both Phishing and Spear Phishing campaigns in parallel.
A Phishing campaign will be automated, target most/all staff and generic. It will raise awareness for the masses against the most
common phishing attacks.
A Spear-Phishing campaign will be manual, target only key staff and tailored. It will raise further awareness to high value target
against the most sophisticated phishing attacks.
This concept of a comprehensive and efficient Anti-Phishing framework is summarised in the diagram below:
{elysiumsecurity} 
Cyber Protection & Response
 RSS Feeds
RSS Feeds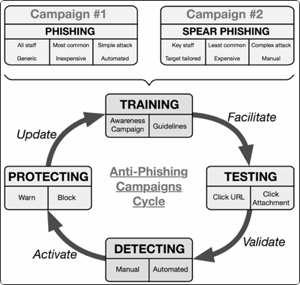 How to build an efficient Anti-Phishing Framework?
How to build an efficient Anti-Phishing Framework?