>> FULL DOCUMENTATION AVAILABLE HERE <<
The BUGS Cipher has two main cryptographic primitives, a Key Scheduler and a symmetric-key encryption function.
It uses an Initialisation Vector (IV) to dynamically change the behaviour of both primitives. It is a highly configurable cipher where the user can decides different default settings which can also be set to dynamically change. For example, the number of round is set to two by default, but it is possible to specify a different value on execution, i.e. R=5. We can also allow or not the algorithm to dynamically change that base value depending of the IV.
The key scheduler is designed to extend or stretch the key. In the symmetric-key encryption function, it is used to generate key buffers in an attempt to diffuse repetition.
The symmetric-key encryption function has two sub-functions, only referred from then on as encryption functions; they can be used independently or combined one after the other. The first of those encryption functions is similar to a block cipher used in a stream cipher mode while the second is similar to a chain block cipher.
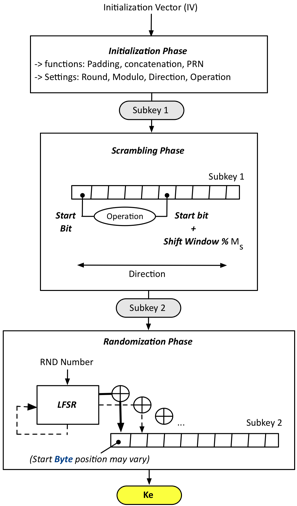
Key Scheduler
The Key scheduler has three Phases: Initialisation, Scrambling and Randomisation.
The initialisation phase requires an Initialisation Vector (IV) and the size Ns of the subkey the user wants to generate. The IV can either be an initial key or a random number both of size Ni such as Ns/2 <= Ni <= Ns
- Operation, O (Swap or Logical Ops) = byte1
- Direction, D (Left or Right) = byte2
- Modulo size, M0 (Big or Small) = byte3
- Nb or Round, R (max x2 value specified by user) = byte4
The main part of the key scheduler is the scrambling phase. Using SK1:
The last part of the key scheduler is the randomisation phase. Using SK2:
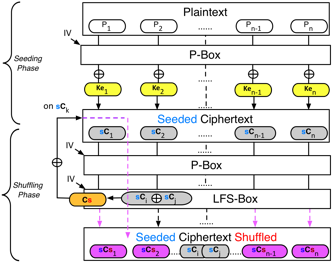
Symmetric-Key encryption function
It consists of an Initialisation phase and two Encryption functions: Seeding and Shuffling. It can operate in different modes where the encryption process uses one or both of the encryption functions. If using both, then the seeding phase is done first and the resulting seeded ciphertext is used as an input into the shuffling phase.
The Initialisation phase consists of the following:
The Seeding phase is similar to a Block cipher used in a Stream cipher mode where a keystream is applied to the plaintext blocks in a pseudo random sequence.
The Shuffling phase is similar to a Chain Block Cipher as described below.
- One of the plaintext blocks used to create Keshuffle is selected as the next block to be encrypted
- Once a plaintext block has been shuffled it cannot be used to generate a new Keshuffle
- And until all the plaintext blocks have been encrypted but two.
>> FULL DOCUMENTATION IS AVAILABLE HERE <<
