Last month, the UK government addressed a letter to all CEOs and Chairs or leading UK companies emphasising that hostile cyber activity is increasing in frequency, sophistication, and impact. It also stated that cyber resilience is a critical enabler of economic growth and that organisations recover better when they have planned and rehearsed for worst-case disruption.
Although it references services and bills that are UK centric, there are some interesting points and information that could be considered and/or used in any country.
The letter asks companies to take three specific actions:
- Make cyber risk a Board-level priority by using the Cyber Governance Code of Practice.
- Sign up to the Early Warning service of the National Cyber Security Centre (NCSC) – a free service giving early alerts of potential attacks on your network. Your country may offer a national CERT service that is similar and if not but it could also be replaced with a ...
>>[READ MORE]

 RSS Feeds
RSS Feeds Cyber Security Governance resources from the UK Government
Cyber Security Governance resources from the UK Government
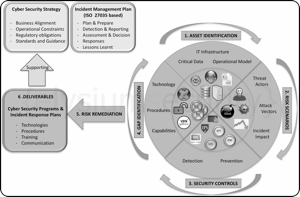 Cyber Security Planning - A simple 6 Steps Approach
Cyber Security Planning - A simple 6 Steps Approach
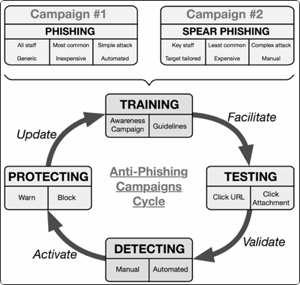 How to build an efficient Anti-Phishing Framework?
How to build an efficient Anti-Phishing Framework?