Special guest announced for the next MU.SCL event!
Dr Kaleem Usmani from CERT MU will be presenting on Incident Handling.
You can register now HERE !
This FREE to attend meeting will take place on the Thursday 26th of April 2018, from 6pm to 8pm, at the Flying Dodo Brewing Company in Bagatelle, Mauritius.
We are working on a streaming option for those of you who cannot physically attend.
The first talk will present how information shared on social media platforms can easily be obtained and used against you. We will also take a look at recent world events and how this data can be aggregated and why this is dangerous.
The second talk will discuss incident handling in t...
>>[READ MORE]
{elysiumsecurity} 
Cyber Protection & Response
All News (146 Posts)
 FREE Cyber Security Event - 3rd Episode!
FREE Cyber Security Event - 3rd Episode!
 MU.SCL - Second Meeting for the Mauritius Cyber Security Club
MU.SCL - Second Meeting for the Mauritius Cyber Security Club
Following the success of last month event, ELYSIUMSECURITY is happy to confirm the second meeting for the Mauritius Cyber Security Club: MU.SCL
This FREE to attend meeting will take place at the Flying Dodo Brewing Company in Bagatelle.
In this second edition, the following two talks will be presented:
The first talk will provide a high level overview of important Cyber Security regulations, standards and best practices relevant to most industries nowadays. At the end of the presentation, attendees should be able to take away key information and follow-up with any questions/worries/debate they may have on the subject.
The second talk will be more technical and focus on how everyone can install an Intrusion Detection System in their home using Open Source software. This talk will hig...
>>[READ MORE]
 MU.SCL - The Birth of a Cyber Security Club in Mauritius
MU.SCL - The Birth of a Cyber Security Club in Mauritius
ElysiumSecurity is proud to announce the creation of a Cyber Security Club in Mauritius: MU.SCLE
This Club has been created to help Mauritian IT Professionals to share information and learn about Cyber Security through an Open Platform and the creation of a Cyber Security Community.
It is a free monthly event open to everyone , usually two talks of 45 minutes each with a mix of technical and non technical talks. Attendees will be able to ask questions, learn and apply practical knowledge as well as do some professional networking.
The first event will take place on the 15th of February 2018, at 18:00 at the Flying Dodo in Bagatelle.
Please REGISTER HERE so we can have an idea on how many people to expect.
We hope to see you there, for what should be a fun, friendly and casual event whe...
>>[READ MORE]
 FIRST Technical Colloquium 2017 in Mauritius - Our presentation on IDS
FIRST Technical Colloquium 2017 in Mauritius - Our presentation on IDS
ElysiumSecurity was invited by the Mauritian National Computer Security Incident Response Team (CERT-MU) to present at the FIRST Technical Colloquium 2017 which took place on the 30th of November 2017.
We gave a presentation on how IDS can be used both as a traditional defensive tool and also a more original offensive tool.
The aim of this presentation was to introduce the attendees of the various free and Open Source IDS offerings and to highlight the benefits and key components of a successful IDS implementation.
It was also emphasised on how easy it is to get started with an IDS both from a software and hardware point of view.
Below is a link to our presentation. If you want a more complete narrative please fee free to contact us for more information.
We would like to thanks the Mauritian National Computer Board ...
>>[READ MORE]
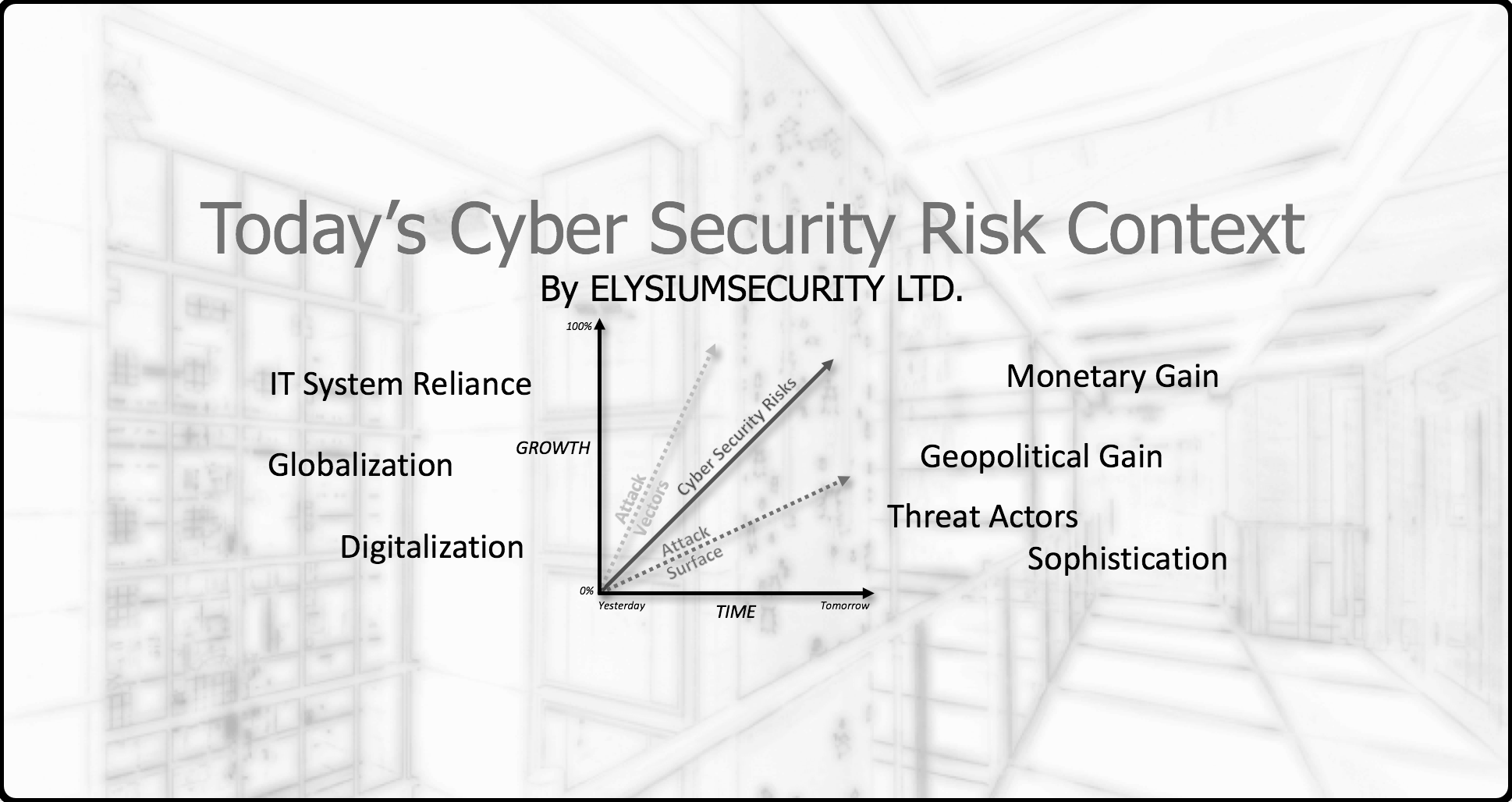 Today's Cyber Security Risk Context
Today's Cyber Security Risk Context
In an attempt to make a wordy presentation slide into something more palatable,
I created this infographic to illustrate the main contributing factors of the growing attack surface and attack vectors faced by many organisations today.
This contributes to an overall growth of their Cyber Security Risks posture.
ElysiumSecurity Ltd can help your organisation with assessing its attack surface and attack vectors to better understand its overall Cyber Security Risk posture and the remediation steps that should be prioritised.
Contact us today for a free consultation at: consulting@elysiumsecurity.com
...
>>[READ MORE]
 GDPR and what it means to companies in the Indian Ocean and Africa
GDPR and what it means to companies in the Indian Ocean and Africa
With fines for non-compliance of up to 4% of a company’s annual global turnover or €20 Million (whichever is greater), and applicable regardless of the company’s location (i.e.: Mauritius). GDPR is a regulation that can no longer be ignored from any companies processing personal data of EU Residents (i.e.: travel agencies, hospitality, banking, health care, insurance, etc.).
This article provides key facts as well as some resources to get started on the road to GDPR compliance.
---
1. Key facts about GDPR;
2. Relevant Definitions;
3. The route to GDPR compliance;
4. Going further.
---
1 - Key facts about GDPR
>>[READ MORE]
 Are Cyber Security Challenges and Opportunities in Mauritius and Africa different from Europe?
Are Cyber Security Challenges and Opportunities in Mauritius and Africa different from Europe?
Spoiler alert: the answer to this question is "not really". However, the subtle differences that do exist are important to acknowledge in order to successfully implement or provide Cyber Security in those locations.
I was interviewed recently for an upcoming article about Cyber Security in a regional African and Indian Ocean magazine called Eco Austral. As I answered the journalist's questions I wondered how different those answers would be if it was for a European magazine.
In this blog article, I will first provide the answers to the four questions I was asked in the wake of recent Ransomware attacks that generated a lot of public attention. I will then expand on those questions and will be looking at the different Cyber Security contexts for those regions in terms of advantages and disadvantages to, finally, identify common opportunities and challenges.
PART 1 - CYBER SECURITY...
>>[READ MORE]
 When Business and Family priorities come together
When Business and Family priorities come together
A few month ago, when my child climbed into the boot of our family car at the airport and pretended to be a suitcase so I could take that “suitcase” on my business trip, it is when I decided I had to radically change how I was doing my job.
As I am turning an important chapter in my working life I thought I would share part of the journey that drove me to first leave a stable and somewhat senior position for a large international company in the UK for a “glamorous” CISO position in a relatively small organisation on the other side of the world, in Mauritius. Then almost a year later, deciding to leave the safety of a full-time job and create my own company.
For 15 years, I worked for BP in the UK in various Cyber Security roles, life was very good, the benefits excellent, the job challenging and I forged numerous good friendships. There were little reasons to leave. Except maybe the prospect of a more outdoor family life in a sunny and beautiful tropical ...
>>[READ MORE]
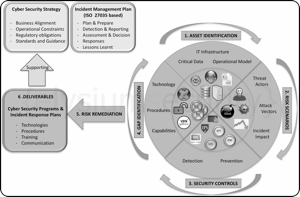 Cyber Security Planning - A simple 6 Steps Approach
Cyber Security Planning - A simple 6 Steps Approach
Having a plan, or not, to secure your enterprise and respond to an incident could be the difference between closing down your company or seeing that incident through!
Most large organisations invest considerable amount of time, money and resources to define a Cyber Security Strategy resulting in several Cyber Security Programs and Incident Management/Response Plans.
All of which are in support of a wider Business Continuity Plan (BCP).
This results in procedures, documentation, backup systems, regular incident simulations and dedicated teams.
As long as these initiatives are kept up to date and still relevant to the organisation mode of operation then it should help a company survive most incidents.
By contrast, smaller organisations and especially start-ups tend to focus first on getting the "job done" and then think of what to do in case of an emergency or incident.
Their Cyber Security Programs and Incidence Response Plans are often limited to t...
>>[READ MORE]
 The 2015 SANS Holiday Hack Challenge Write-Up
The 2015 SANS Holiday Hack Challenge Write-Up
For the last 12 years, SANS/Counterhack offers a hacking challenge over the Christmas period. It is a great event, fun and with an increasing level of difficulty which lets everyone having a go.
This year, The 2015 SANS Holiday Hack Challenge was built around a great 8-bit retro web gaming platform where you had to run around a virtual town to find the various hacking challenges.
The plot was centered around a fictitious toy, a gnome, that everyone wanted to have in their home for Christmas. However, two kids found the toy was "behaving" strangely and something was going on.
Through the challenge you will learn that the gnomes had in fact a hidden built-in camera and were transmitting photos to 5 super gnomes (servers) by connecting to free surrounding WIFI netwo...
>>[READ MORE]
 RSS Feeds
RSS Feeds